Read time: 6 minutes
Today I’ll show you how to properly secure and access your .NET application secrets via Azure Key Vault.
You probably know you shouldn’t be storing API keys, connection strings, and passwords in your code, so hopefully you use something like the .NET Secret manager during local development.
But how to get ready to use those secrets in the cloud while keeping your code clean and following best practices?
Azure Key Vault is the solution for this and the best thing is that it integrates beautifully with ASP.NET Core, so you can retrieve those secrets as if you were reading your appsettings.json config values.
In this tutorial, I’ll walk you through the entire process step-by-step.
Let’s get started.
What is Azure Key Vault?
Azure Key Vault is a cloud-based service designed to store and securely manage application secrets.
It’s the right place to store your connection strings, API keys, and passwords, so they stay away from your code base, but you can also store encryption keys and certificates.
In addition, Key Vault can do:
- Versioning. Each time you update a secret, a new version is created, and your code can reference either the latest version or whichever previous version is needed.
- Access Control. Define granular permissions through Azure RBAC (Role-Based Access Control) to determine which users or applications can access specific secrets.
- Monitoring and Logging. Track who accessed secrets and when through detailed audit logs and Azure Monitor integration.
Let’s see how an ASP.NET Core app can read secrets from a Key Vault, step-by-step.
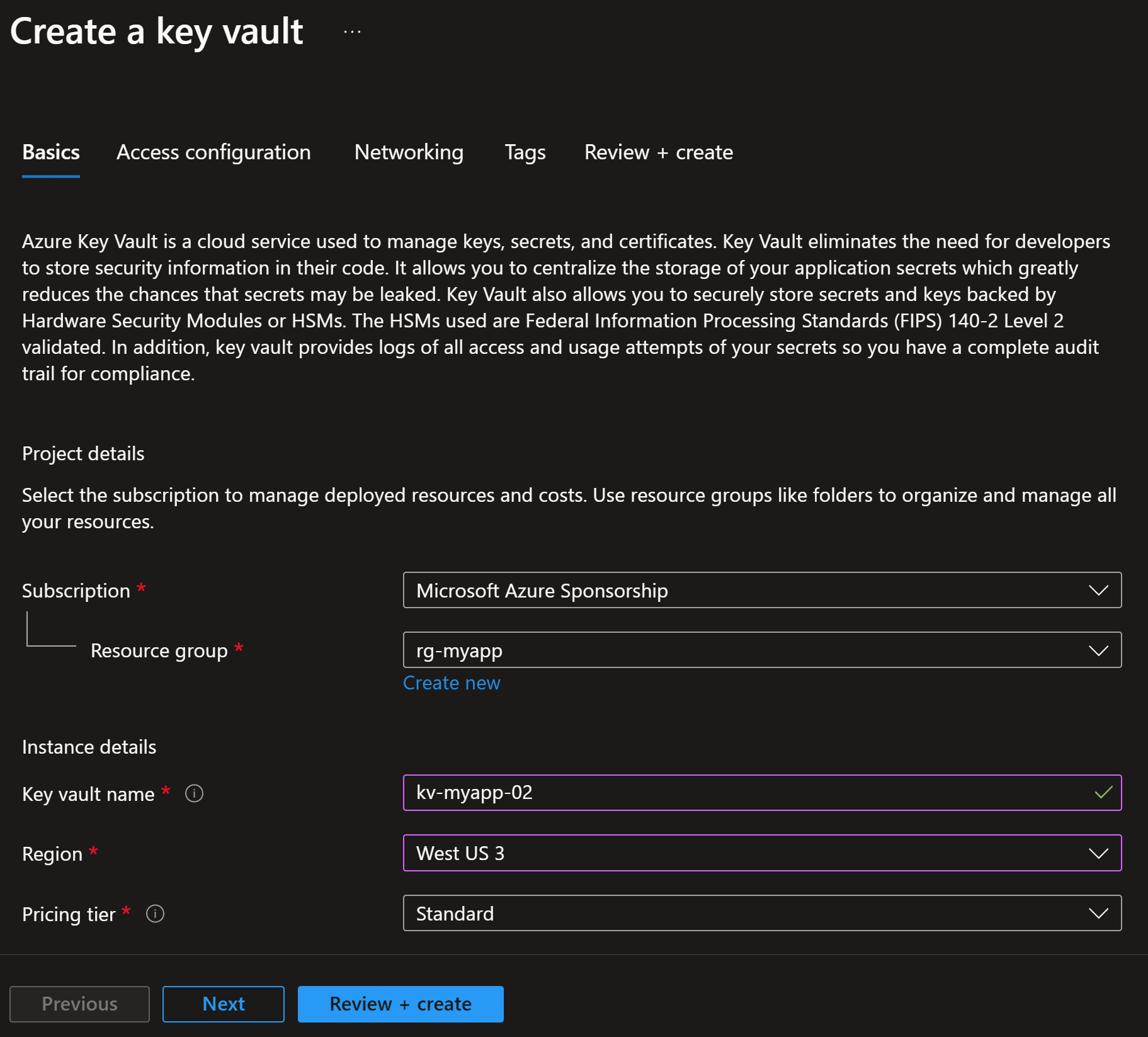
Step 1: Create your Key Vault
If you don’t have one already, you can quickly create a Key Vault from the Azure Portal by providing a name, a region, and your pricing tier:
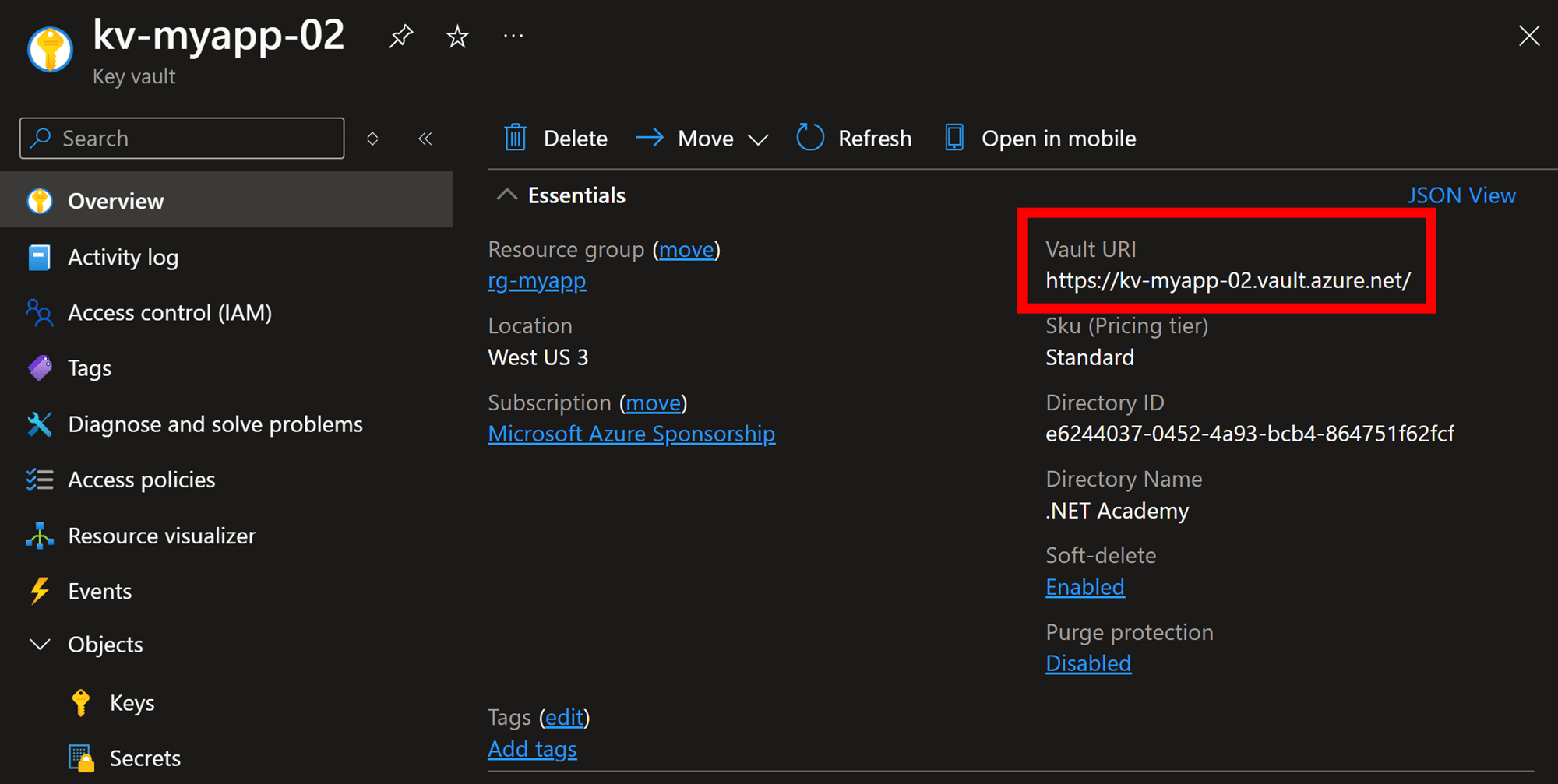
Once created, the main detail you will need later in your app code is the vault URI, available in the Overview blade:
Next, you should configure your permissions.
Step 2: Add permissions
Key vaults are very secure by default. This means that even if you created the vault, you won’t be authorized to start adding secrets:
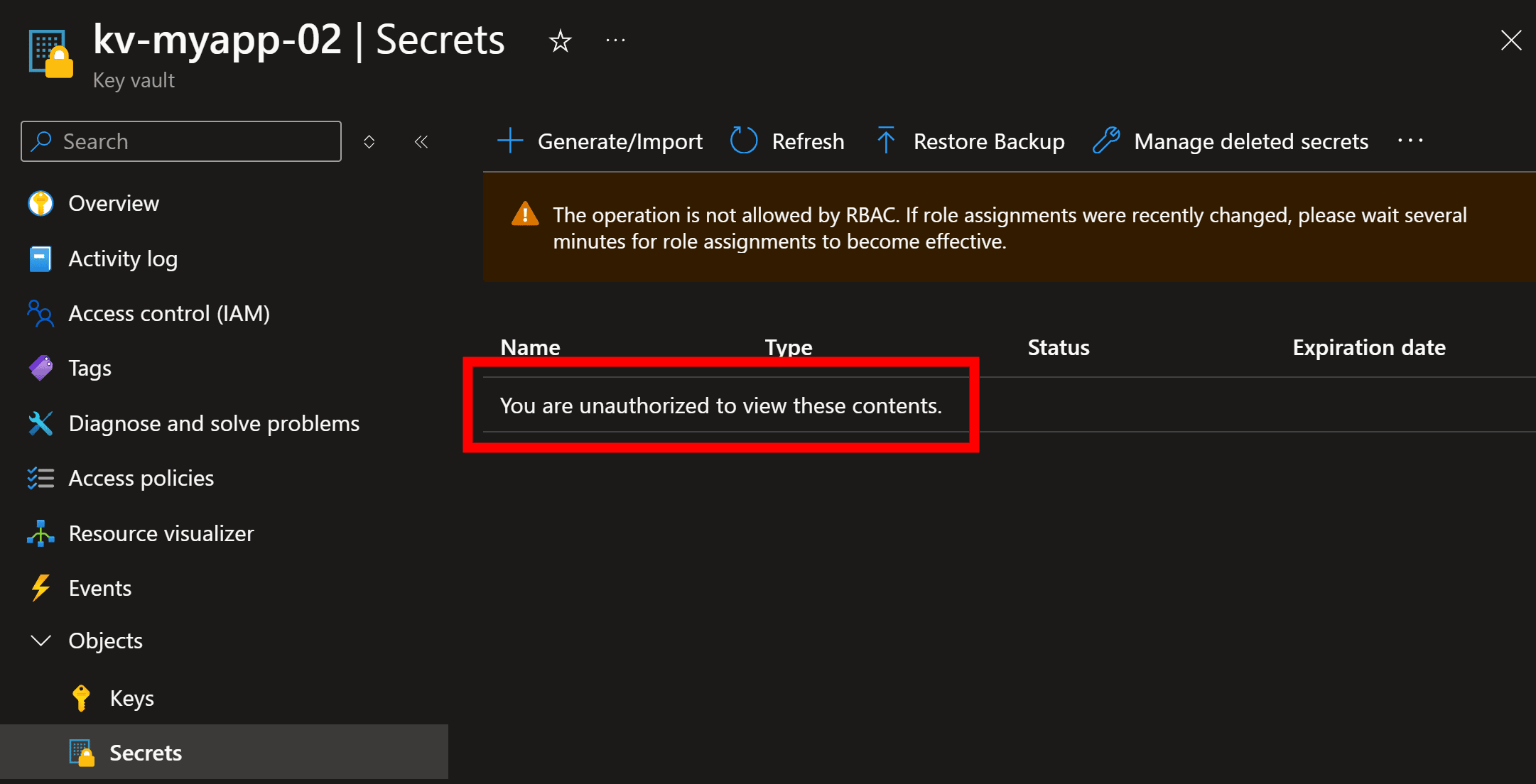
For this, go to the Access control blade, and assign yourself the Key Vault Secrets Officer role:
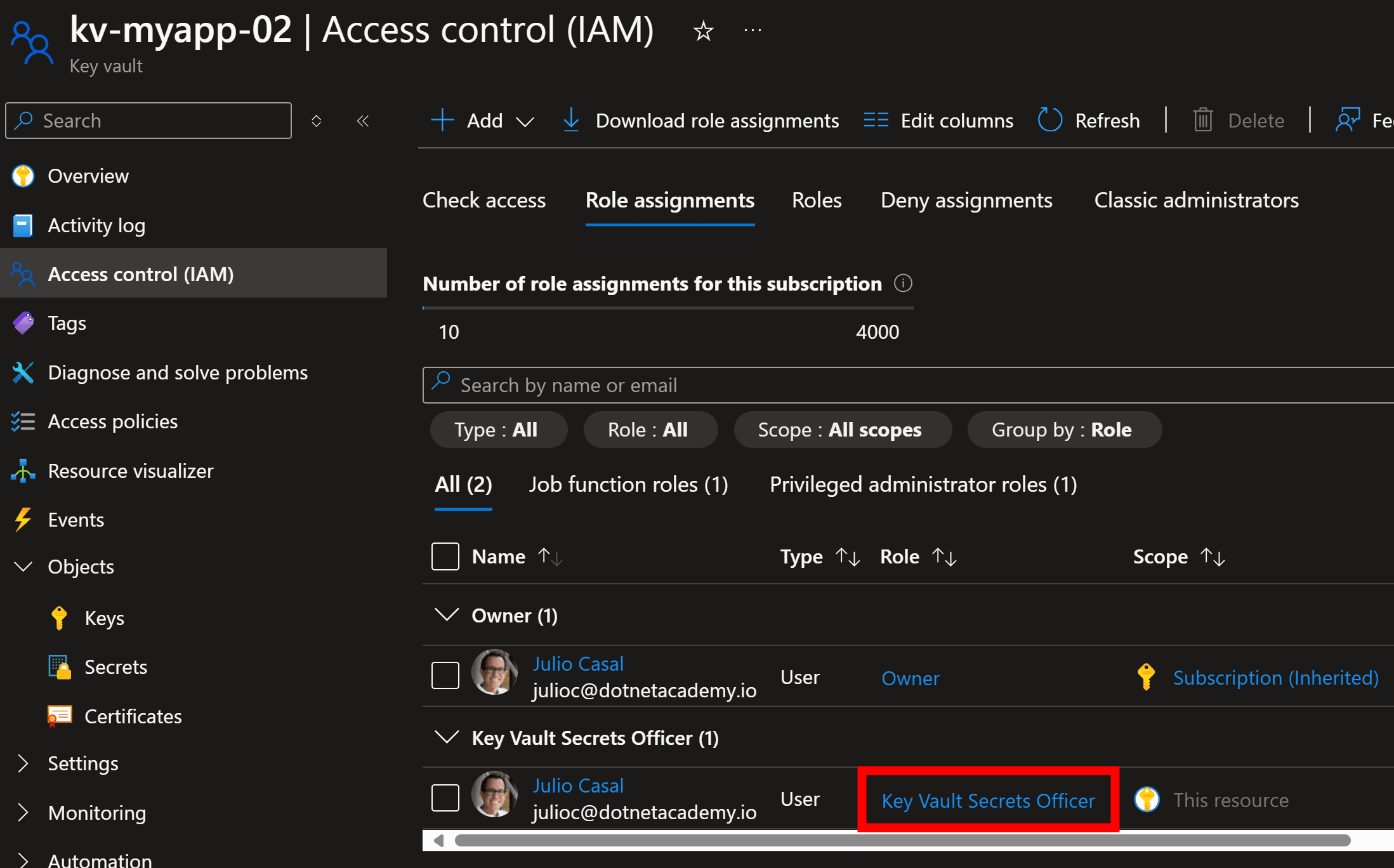
Now you are ready to start adding secrets to your vault.
Step 3: Create the secret
Let’s say we need to store our OpenAI API key in our Key Vault, which our app will use for all its generative AI needs.
Let’s add that secret on the Objects –> Secrets blade:
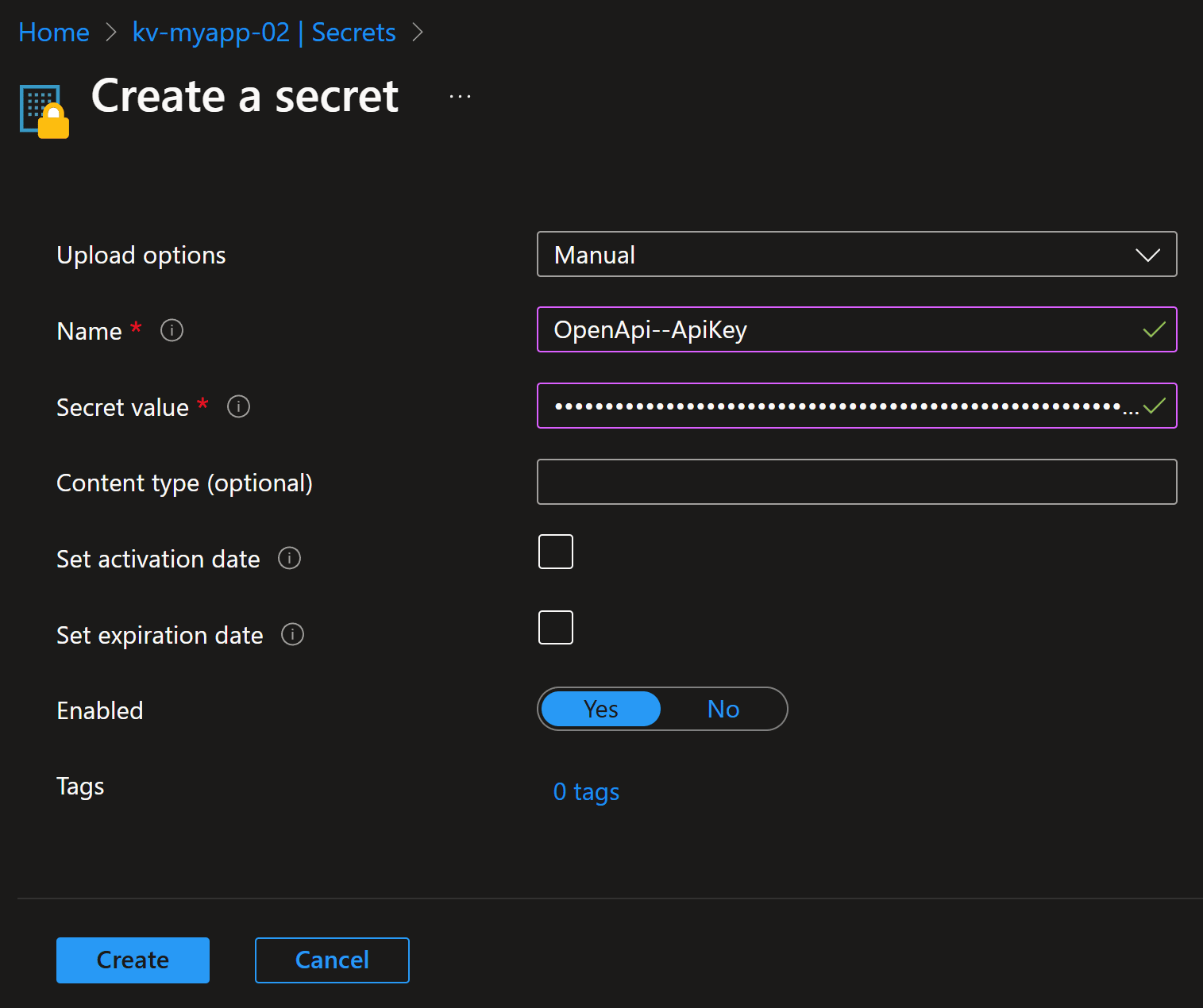
Why did we use that specific pattern, with double dashes in the middle, for the secret name?
Well, because that is a pattern that ASP.NET Core will be ready to recognize via the Key Vault Configuration Provider, making reading the secret a trivial task for our app.
So using the OpenApi–ApiKey secret name is essentially the same as adding this configuration to your appsettings.json file:
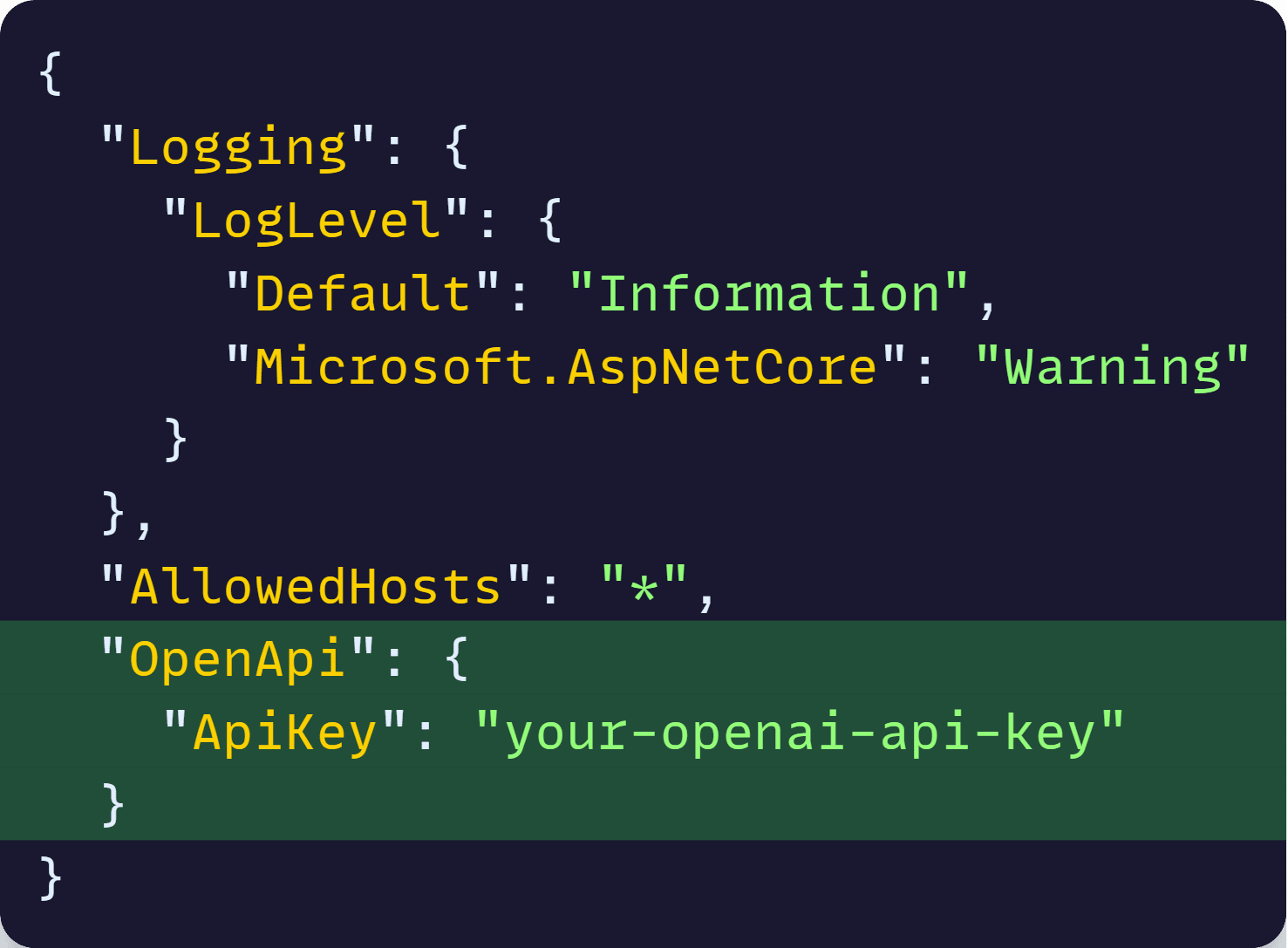
But of course, we won’t add anything to appsettings.json. Let’s see what we’ll do instead.
Step 4: Read the secret
Start by installing these two NuGet packages:
- Azure.Extensions.AspNetCore.Configuration.Secrets
- Azure.Identity
Now add this to Program.cs:
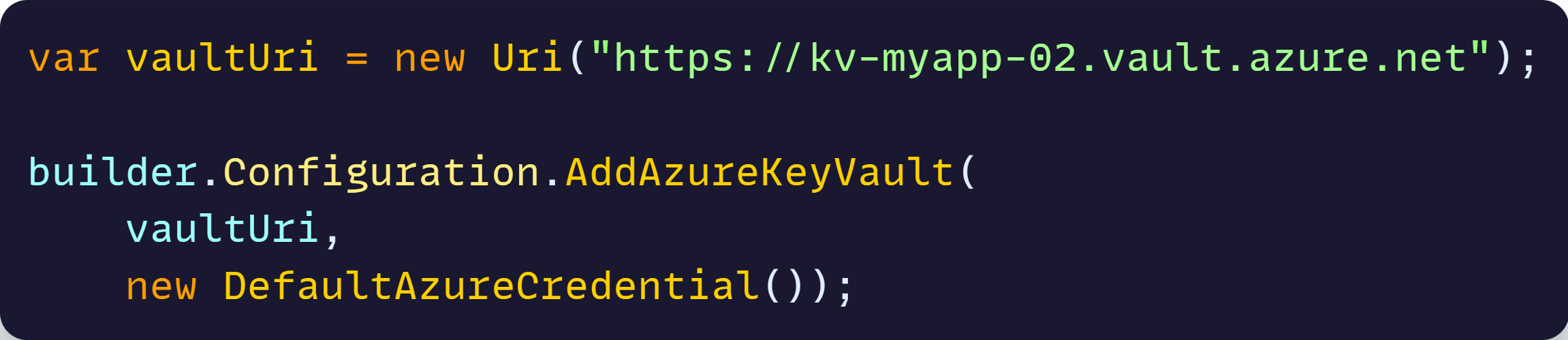
That will add your Key Vault as a new configuration source to your .NET application. From here on, any secrets in your vault can be read from the standard configuration system.
Which means we can do things like this:
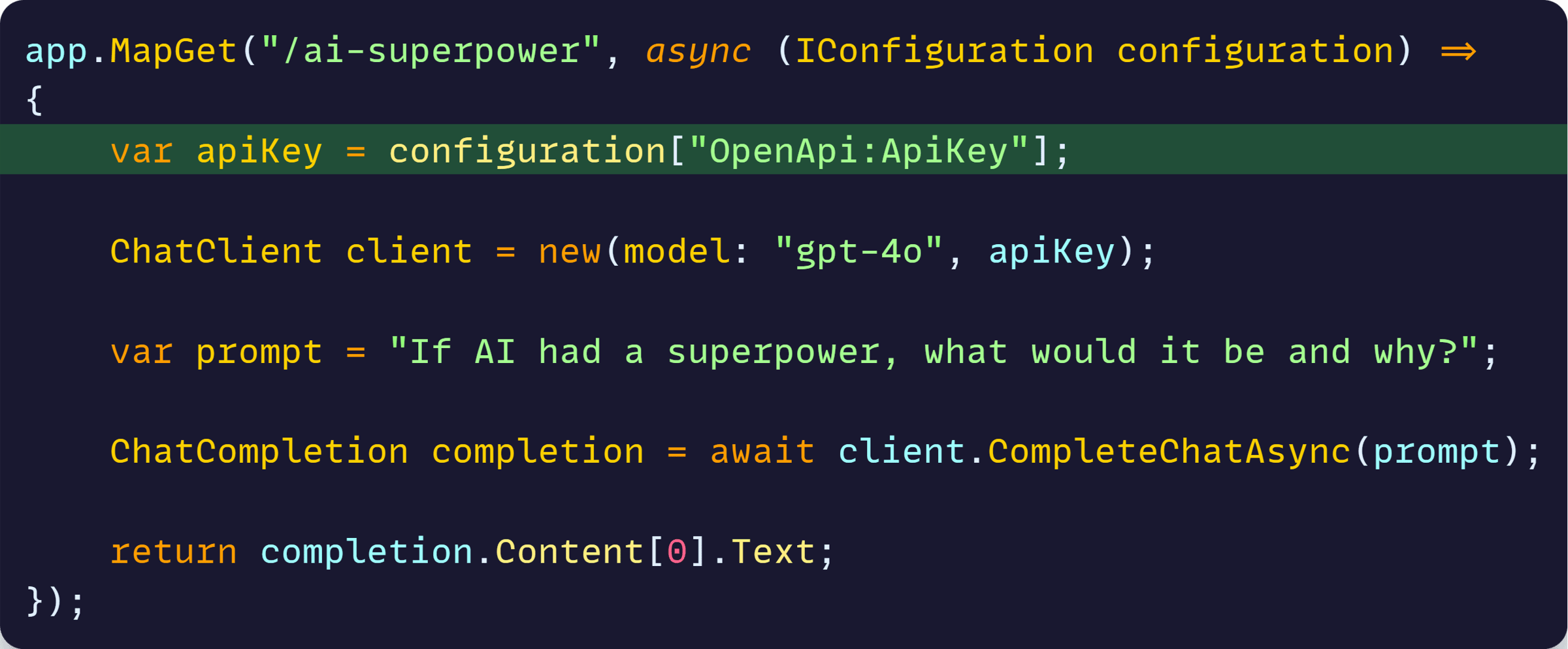
Which at runtime looks like this:
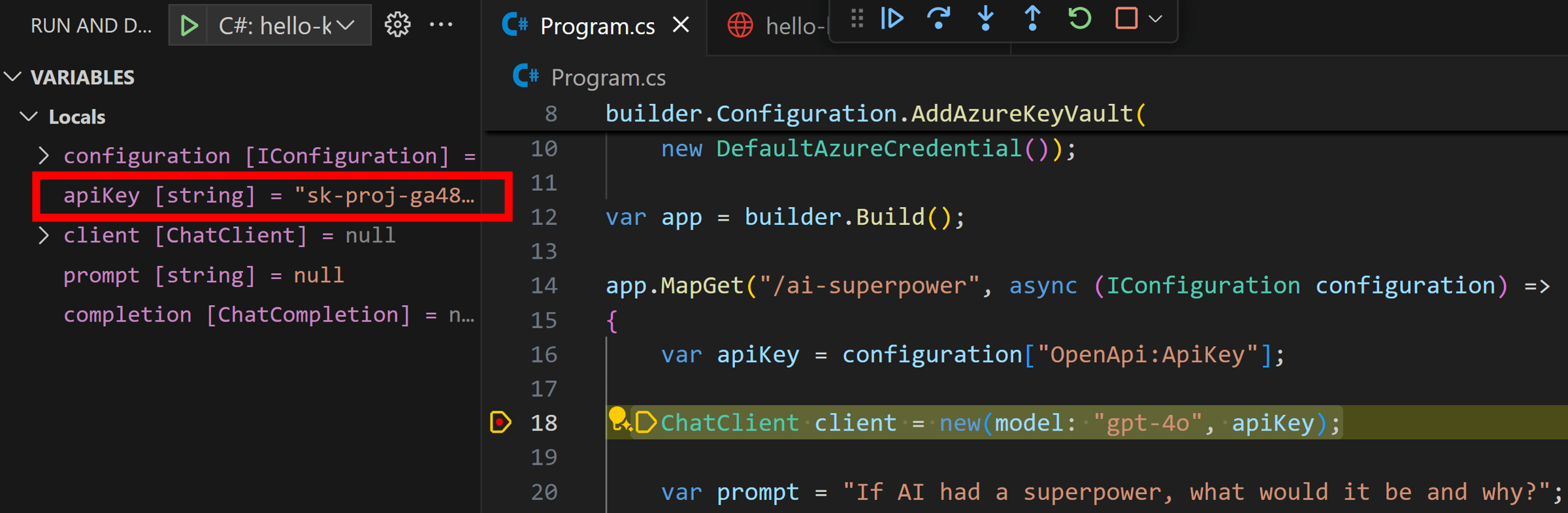
Mission accomplished!
Step 5: Cloud deployment
There are several ways to deploy .NET Web apps to the cloud. I covered the simplest way last week, so I won’t repeat that here.
But to successfully use your Key Vault integration in the Azure cloud, you want to make sure you associate a managed identity with your deployed application, as I covered here.
Then grant that managed identity the Key Vault Secrets User role in your Key Vault:
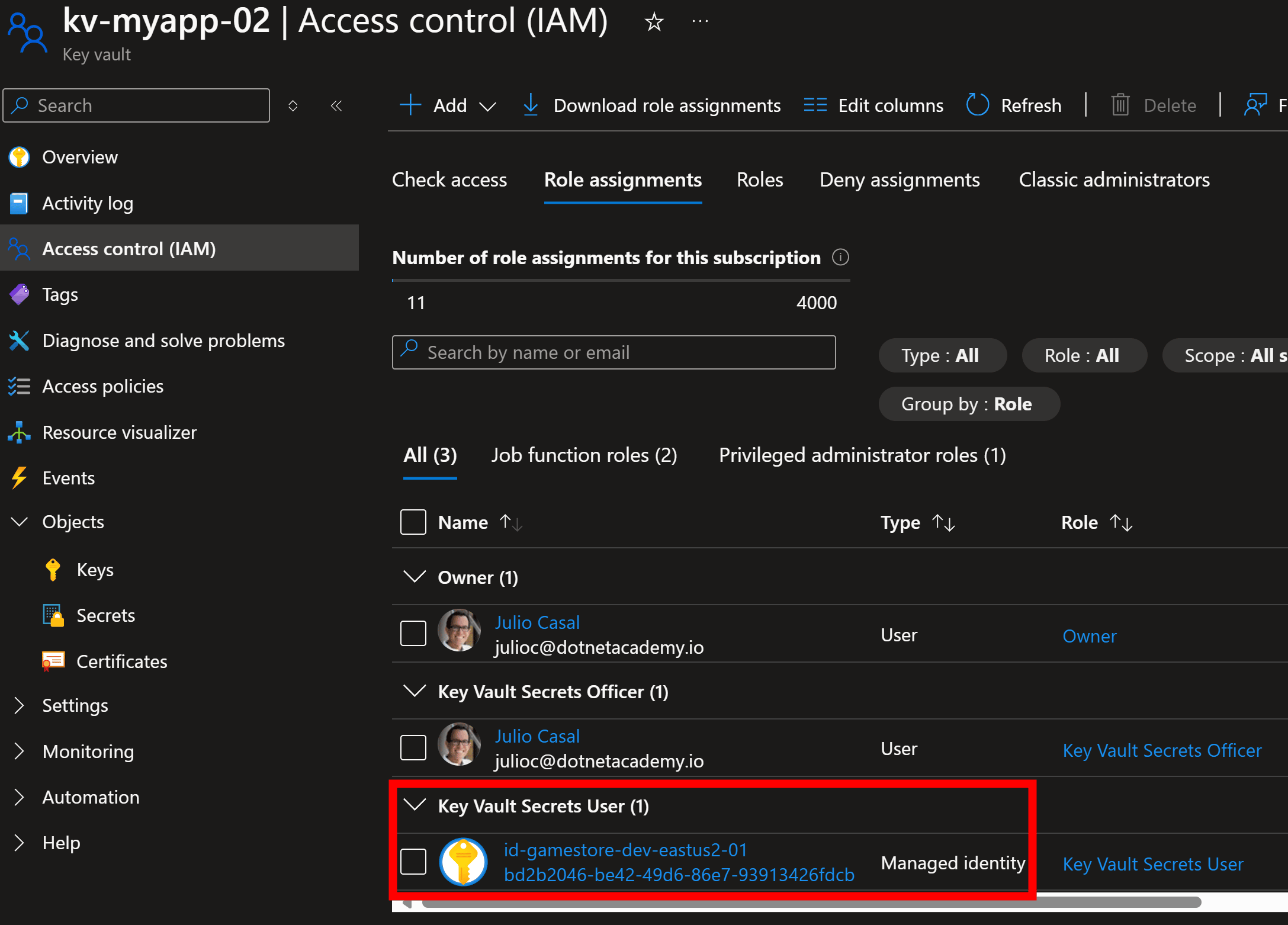
And then your deployed app will have no trouble reading secrets into your app configuration, just like it did during local development.
I go over this entire process, for a real-world e-commerce application, in the bootcamp.
Until next time!
Whenever you’re ready, there are 3 ways I can help you:
-
.NET Backend Developer Bootcamp: A complete path from ASP.NET Core fundamentals to building, containerizing, and deploying production-ready, cloud-native apps on Azure.
-
Building Microservices With .NET: Transform the way you build .NET systems at scale.
-
Get the full source code: Download the working project from this article, grab exclusive course discounts, and join a private .NET community.